Course Review - Zero2Automated Advanced Malware Analysis Course
The OSCP experience for reversing malware. Try harder!
Disclaimer: The views, methods, and opinions expressed at Anchored Narratives are the author's and do not necessarily reflect my employer's official policy or position.
Introduction
After leaving Shell, one of my personal goals was to become a bit better at malware reversing. So I enrolled in a virtual course from Kaspersky called “Targeted Malware Reverse Engineering” and the Advanced Malware Analysis course by Zero2automated. The course by Kaspersky focuses on nation-state actor groups, whereas Zero2automated also focuses on cybercrime malware like Trickbot and other cybercrime actors. According to their course description, their course “Initially created as a response to the lack of affordable advanced malware reverse engineering training, the Zero2Automated course was developed by malware reverse engineers, for malware reverse engineers - with a large focus placed on practical analysis".
What also intrigued me about this certification is that the final exam had a theoretical and practical part. You have to examine malware as the final challenge. I’m not aware of any other malware reversing courses that have practical exams.
Besides that, every other week or month, I noticed someone on LinkedIn receiving the certification listed on this article's cover, and I was just intrigued by it. But, unfortunately, I see certifications as the bare minimum of knowledge, and sometimes knowledge on a particular topic is minimal.
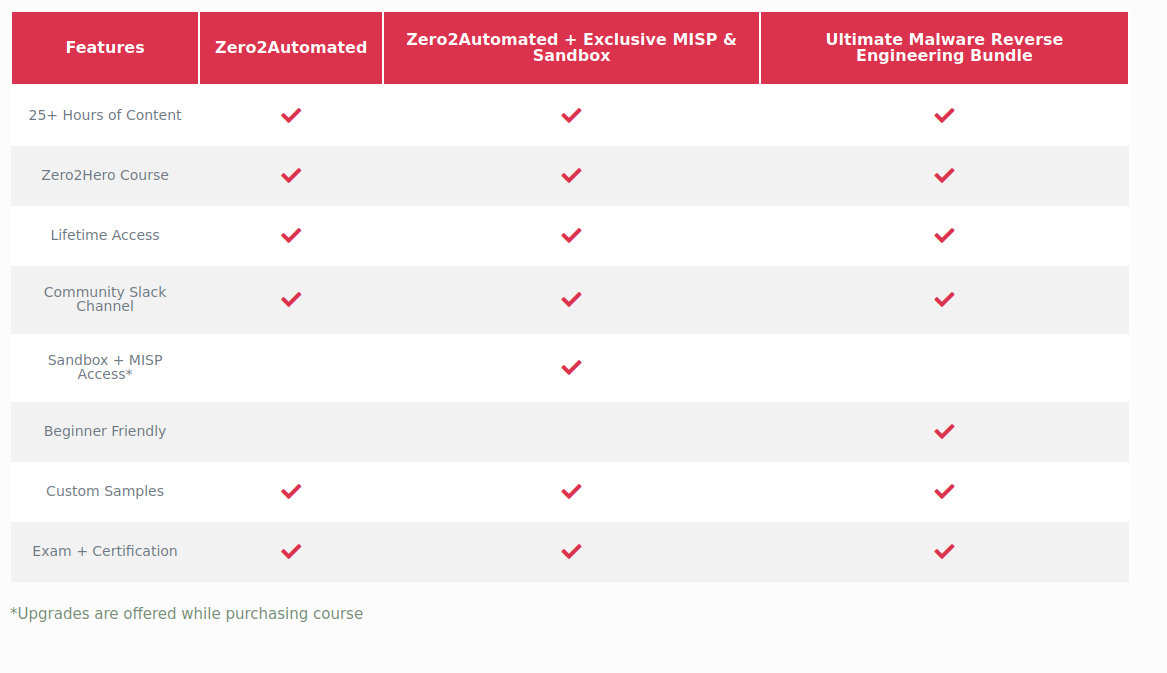
The price for the complete training, including exams, costs around 177,35 Euros, so it seemed like a very reasonable proposition compared to 6K malware courses.
This anchored narrative will review the Zero2Automated advanced malware analysis course by course setup, learning objectives, and lessons learned. I will end it with a Q&A section with one of the course developers, Daniel Bunce. This review will not give away any spoilers. Let's go.
Course Setup
Once you onboard into the course, you will receive instructions via e-mail that provide you access to the learning platform of Zero2Automated. Before logging in to the learning platform, make sure you have set up your Virtual Machine. I downloaded my VM from the following website and installed all tools via the flare script. Once you're settled you log in to the portal where the instruction video, powerpoints and documents reside. Intially every other day the chapters get unlocked.
Every chapter starts with a video presentation about understanding algorithms, unpacking malware, obfuscation techniques, or persistence mechanisms. Some chapters focus intensely on different process injections, rootkits, or malware that can be decompiled to source code, like .Net or python malware. Chapter 8 entails threat intelligence and how you could build solid Yara signatures. A very enlightening chapter around shellcode is also presented. After each chapter, malware samples are provided and you are challenged to reverse engineer the sample similarly. This is where Zer02Automated will put you at the test. Midway through the course, you can take a practical analysis of a previous exam. Practicing this will prepare you for the final exam later on.
I enrolled on a Zer02Automated exam package where I also could leverage “Any.Run” sandbox functionality. This subscription also provided me access to the Zero2Hero course content videos who supposed to be aimed at the beginner-level malware analyst. However, I found those still very technical, to be honest.
Once you are enrolled, you are onboarded to a Slack channel with people that also enrolled in the training. You can reach out to the course creators or other participants within the channel. Students are also sharing relevant threat intel, so it has the potential of becoming a trusted community, although current students’ interactions or sharing intel were not that often.
Course instructors
Daniel Bunce and Vitaly Kremez are actively developing the Zero2Automated courses. Jason Reeves wrote a pdf book shared on the platform that details how to analyze and dissect known malware families. Daniel is presenting 80 % of the time and has a high pace. It is sometimes difficult to follow everything that is happening. Daniel extracts and automates configs from malware and writes that in python. The speed is a bit too high sometimes to follow without going back and forth in the instruction video, which I find annoying. Vitaly has a lower pace of presenting and explains well. Overall, both gentlemen assume you already have some background in malware reversing as that is skipped in the instruction videos or even the zero2hero material.
Course Review and Lessons learned
I cannot say that I enjoyed this malware course, but I learned a lot. There are many reasons, but the main reason is that the practical exam was a bit too difficult for me initially. I’m not a quitter, so this initial failure resulted in reading more about malware analysis and reassessing malware samples in IDA, Cutter, and X64dbg.
During the course, I noticed that once you assess different malware samples and understand relevant API calls, injections, or obfuscations, recognizing known patterns goes faster, just like learning French.
You are also taught to write some Python automation scripts which are also helpful for config extractions. Besides becoming a better reverse engineer, I learned how to use the correct tools for the reversing job, IDA/Cutter and X64dbg.
In the course, you are also taught to reverse-engineer programs within different programming or heavily obfuscated scripting languages (C, .NET, Powershell, Python, JavaScript, C++). I also analyzed malware samples compiled for 64-bit architecture and, of course, shellcode. For shellcode analysis, I learned how to use blob64runner. That's a tool that lets you run shellcode, which can be attached and analyzed in the x64dbg. Overall the course is structured really well but could use a bit of theoretical background of why malware authors make certain design choices for encryption or obfuscation.
The Final Exam
Once I felt ready to take the exam (basically finishing all the video instructions and samples), I submitted the link with the examination request. The first part of the exam was theoretical, and that was not a real problem, but also eluded to some difficulties for the practical exam. After a positive result, I entered the practical exam. I will not share any details about the exam, but it felt like the OSCP exam 24 hours experience again. First challenges were met, and now what? Realizing that you are stuck where you know you still need to produce a proper understanding of the malware without guessing and making sure your findings are accurate and you can reproduce it. This is where my frustration kicked in. How much time do I need to spend on this to achieve this? At some time, I was so fed up with it that I basically gave up, but I cannot quite as mentioned earlier. With some additional time committed to the malware, reading up, and repeating a lot of things, I finally progressed to the final certification bringing peace to my household again. Serenity now!
Buy or Not
This course is not aimed at people who have no experience with malware reversing but is primarily aimed at people who have already some experience with it but need to improve their game. From my professional background perspective as a manager of technical teams, I believe this course would help many cybersecurity specialists mature their reversing skills. Also, the pricing for the offered learning environment ($201.71) is very competitive compared to the SANS malware track, for example, which costs nearly 6k depending on the delivery method.
So a definite buy, if you are a disciplined person and can systematically work online besides your day job. The learning environment is pleasant, and malware cases are fascinating to investigate.
Q&A with Daniel Bunce (Overfl0w)
During the malware course, I asked if Daniel would be interested in interviewing for the Anchored Narratives site. He agreed, but I told him that I first needed to finish the practical exam.
Can you tell me a little bit of background about yourself? How did you end up creating advanced malware reversing training and become a malware researcher?
For sure - I actually started off on the red team side, interested in everything from bug bounties to exploits, but soon realized with my setup (one laptop) there was only so much testing I could do, so I focused on malware development. I then came across the malware RE field, which I didn't think actually existed to begin with, and soon started to hone my skills on reversing different types of malware, to begin with, and soon started to hone my skills in reversing different types of malware. I posted quite frequently to my personal blog back then, and got an overwhelmingly positive response - I worked on formatting the blogs in a way that would explain different concepts rather than just saying what the malware did; so how did it do what it does, how we can identify certain functions of importance, etc. A few years back I decided to try and create a beginners course, introducing the core topics of malware analysis, as a lot of the materials out there were blogs or books, which I can understand are quite difficult to follow along properly. I didn't think it would take off like it did once released, but afterwards I began planning a more advanced course, as well as working with SentinelOne and VK on the Zero2Hero course.
How did you, Jason, and Vitaly come together?
I had been speaking with Vitali since before I released my first course, but after the successful release we decided to partner up and work with SentinelOne on the Zero2Hero course as mentioned above - from there we decided to plan and develop the Zero2Automated course - Vitali knew Jason quite well, and a few months before the release of the course he had mentioned a book Jason had developed walking a user through different malware families, and we all decided it would be a great addition to the course!
Why did you create the advanced malware reversing training and also at this price range?
Since releasing the beginner course there has been a ton of content released on malware analysis & RE, a lot mostly beginner focused - a few advanced concepts were covered in expensive trainings and/or conferences, but trying to find those concepts online used to be quite difficult. With the training I wanted to create something where all sorts of advanced topics were covered in one place, using up to date malware samples (so not like stuxnet or myDoom), all while making it affordable to students and researchers alike; I've never been a fan of how expensive trainings can be, especially if it's in a virtual format, so I wanted to keep the price as low as possible.
What are the future plans for the Zero2Automated training?
At the moment a few things are in the works - there are a few chapters that need to be cleaned up a bit, as well as additions to the course such as reversing golang malware, analysing some more types of malware (spambots, stealers, rootkits, etc.), plus I'm working on refactoring the exam so that it is held in a much more professional format, with labs and such.
Which techniques are currently not covered in the training and are more often being used by threat actors to bypass security controls?
Hmm this is an interesting one - I'd imagine there's quite a few, for example we don't cover every single LOLBin or UAC bypass, as that would take forever. Additionally, we haven't covered any of the new vulnerabilities such as ProxyLogon, though I would like to add a chapter at some point covering a few of these exploits & how to analyse the infection chain.
What is the most complicated malware investigation you have done and why?
By investigation do you mean REing the binary or a full patient zero to ransomware type of thing? RE wise definitely Dridex, with the amount of obfuscation inside the sample as well as the backend security for the HTTPS & P2P communications making it extremely difficult to pull down any sorts of web injects or additional modules.
How do you keep so calm on students’ inquiries? I was very frustrated during parts of the exam.
Hahaha, I find in order to be a good teacher you've got to have patience - especially in malware analysis; it's an extremely difficult thing to get into, with all the previous requirements from windows internals, malware development, threat intelligence, programming, and being able to understand assembly, and I still do find myself getting frustrated at certain samples (more recently some .NET samples with too much obfuscation!), so I can understand a lot of the feelings surrounding the field :D
Which threat actor group(s) intrigues you the most?
I've always been interested in E-Crime, so definitely have to go with EvilCorp and the Emotet guys, was a huge surprise to see Emotet resurfacing at the end of last year, though I suppose it was fairly inevitable.
How do you analyze malware samples? Solely statically or dynamically as well?
I try to reverse statically as much as possible, only ever using dynamic analysis for confirming my understanding of a function - though it depends on the reason, if it needs to be analysed quickly and there's a ton of obfuscation, I'll usually dynamically analyse it or even drop it in a sandbox to get the critical IOCs before looking into it a bit further statically.
How do you see the future of malware reversing? Do you expect new threats or methods?
I think we'll see a lot more usage of more uncommon languages like Rust and Go, and I expect ransomware is probably here to stay for the next few years at least. I'd imagine there will be a slow shift to OSX targeting malware too, especially from the larger E-Crime families; though for the moment there isn't much of a need as ransomware is too lucrative to pass up for many of them.
Which resource/book/course/person helped you greatly improve your malware reversing skills?
There are a few! The OALabs guys have some brilliant content on their YT channel, and can't forget Malware Unicorns RE101 & 102. Favourite book has to be Practical Malware Analysis by Michael Sikorski, probably considered the Malware Analysis bible by many!
Do you track nation-state hackers, and how do you do that?
Haven't done a ton of research into nation-state actors, though the one that stands out in my mind is Lazarus - specifically the Bluenoroff subgroup who were purported to have performed the Bangladesh bank robbery where they attempted to steal close to $1 billion. The internal reconnaissance they performed was crazy, monitoring activity each and every day, up to the main attack, which partly involved causing a malfunction to the SWIFT transaction receipt printer to slow down detection.
Why do you focus more on E-crime groups than nation-state actors?
Sure - really it was the first thing I started looking at, was more accessible (C2s and campaigns were live whenever someone tweeted about it), unlike APTs which you would normally hear about 2-3 months after the campaign; as its constantly changing there's never really been a dull moment with different actors cropping up each and every day, and developing emulators and trackers is a lot easier and provides some nice TI (Threat Intelligence)