Hunting for geopolitical tensions & cyber actors on Twitter chatter
A look back on three geopolitical disputes in 2020
Disclaimer: The views, methods, and opinions expressed at Anchored Narratives are those of the author and do not necessarily reflect the official policy or position of my employer.
Introduction
This article will give you an insight into how collected Twitter data can be exploited from a cyber threat intelligence (CTI) and threat hunting perspective by detecting geopolitical events. There are, of course, many more applications like vulnerability monitoring or local crime monitoring, but that is out of the scope of this article for now.
Twitter data is seen as open-source data and is leveraged by many journalists and researchers to sense the public on topics. Twitter has roughly about 340 million users worldwide who are sending about 500 million daily tweets on all kinds of topics.
An early study of Twitter users revealed that people are using this platform for three reasons: information sharing, information seeking, and friendship-relationships (community) [1]. This data is, of course, precious for advertisers, journalists, and researchers, but this data has also been of interest to the defense community for intelligence exploitation [2,3,4]. Threat intelligence is the process of directing, collecting, processing, assessing, and sharing information (disseminate) to identified stakeholders that pose a threat to a specific location, people, application, or networks. From a cyber threat intelligence perspective, it is usually to collect information constantly that poses a threat to computers, software, or networks. Those stakeholders are then proactively informed with a course of action (COA).
Although there are many different ways to obtain intelligence from different sources, this article will only focus on collected Twitter data, where it’s used to determine if we can find geopolitical tensions or disputes and correlated nation-state cyber activities. This is, of course, not the basis for intelligence analysis, as you need to obtain information from multiple sources. This makes those assessments more reliable and also less susceptible to disinformation campaigns. But let’s find out how valuable Twitter data is.
From my personal experience, I have noticed too often that assessing intelligence is sometimes simply too much, and there is always something new to the analyst. It feels like drinking from the fire hose, so to say. First of all, you’ll need a plan to detect the most relevant threats, vulnerabilities, or exploits. An exploit is a piece of software that exploits the discovered weakness in the vulnerable program, which can lead to access of information or a system.
Of course, there are commercial solutions used by many organizations (Threat Information Platforms) for threat analysis. These platforms collect data from multiple sources, from Twitter, and provide an analyst with a good insight into the most relevant threats to assess further.
In the next paragraphs, geopolitical drivers are explained and which disputes they might produce. After that, cyberwar will be briefly explained, followed by threat intelligence and some geopolitical cyber cases found by the developed process.
The final paragraph will conclude with some of my personal learnings.
What are geopolitical drivers?
According to Brittanica, geopolitics is the analysis of the geographic influences on power relationships in international relations. The world and countries as we know it always has one of dispute in certain areas. Some countries inherited their prosperity on their geographical location, natural resources, rivers, access to the sea, or protection of the borders by mountains. An interesting book, called “Prisoners of Geography. Ten maps that tell you Everything You Need To Know About Global Politics” by Tim Marshall, was written about it. Currently, you have some, the so-called Great Powers, which possess great economic, political, or military strengths. Examples of those powers are the United States, Russia, and China. Among those countries, you have allies or partnerships.
From a geopolitical perspective, countries seek opportunities for their people from an economic or safety perspective. Governments define these goals as geostrategy. Some examples are The Belt and Road Initiatives or the Five-year plans from China which outlines its strategy from a military, political, or economic perspective. These government goals could be conflicting with the goals of other nations and end up in certain disputes. And it is these disputes that we’re interested in.
According to Willis Towers Watson, a leading advisory and broker company, geopolitical risk is the number one global corporate risk for companies and countries. They have drafted an overview of relevant geopolitical risks, illustrated below, and seen as drivers for defining a certain strategy. The defined geostrategy of countries might end up in disputes between countries or regions. According to them, Cyber is one of the key risks that countries face. This is also experienced by many cyberattacks, such as targeted ransomware attacks, nation-state espionage cases on governments or companies—the latter, usually from economic interest.

As illustrated in figure 2, the risks can have a tremendous impact on the country and its society. Governments will try to control these risks. One way to improve your economic perspective is by spying on other countries to gain a technological advantage in certain key industries. We have seen many cases of espionage by nations. One of the first public reports about economic espionage was highlighted in the APT1 report by security firm Mandiant in 2013. In that report, the attack was attributed to a Chinese Military unit called PLA Unit 61398. Since then, many reports have been published of ongoing nation-state cyber operations to obtain a certain advantage. Also, many by the so-called geopolitical Super Powers. How nation-states plan these operations will be described in the next paragraph.
Objectives of Cyber War
In an interesting thesis from 2017, called “Cyber Warfare Conflict Analysis and Case Studies”[5], the author, Gazula, researches have known cyber warfare cases and uses a history-based conflict, analysis, and decision-support framework, called CASCON. Although CASCON only contains a historical database with kinetic warfare cases (Land, Sea, and Air Operations), the author maps twenty-four well-known nation-state cyber incidents to the framework for further analysis. All these known cases from Shamoon to Stuxnet are analyzed according to that framework. An attacking country is referred to as a “Non Status Quo State,” and the passive country is the “Status Quo State.”
In his paper, the author also describes the objectives of Cyber War in five different phases. These phases might sound familiar for someone in the penetration or red teaming field but are also experienced in Advanced Persistent Threat Investigations.
“Cyber Warfare is mission focused and the success is largely based on the superiority and sophistication of technology used in the planning phase. The criteria for the mission have to be defined in this phase. Compared to kinetic warfare, where a dispute is the basis for the warfare that escalates to become a conflict, cyber-warfare could originate with or without a conflict.A planning phase is when a cyber-weapon is tailored to the opponent’s cyber environment (Target). Knowledge about the target is key during the planning phase. Knowing specific vulnerabilities and scenarios on which vulnerabilities could be seized constitutes a major part of the planning. This phase is also called the intelligence gathering and evaluation phase. The triggers to the planning phase include a new dispute that surfaces between states or an ongoing dispute that had existed. After thorough planning has been achieved the weapon is released into the target environment. The entry point, what vulnerabilities to seize and how it exits the target is determined in the planning phase.The Reconnaissance phase is where the Cyber weapon has been released by the non-status quo side and has found a way to enter the target environment to be able to take control and proceed with its mission. The weapon is scanning the target to take its full form.During the Replicate phase, one or more vulnerabilities in the target environment have been identified and acted upon. The footprint of the weapon has grown significantly and has taken form. The weapon is still in the stealth mode but is in control.The Assault or Hostilities phase is where the weapon is unleashed and it carries out the mission in the target environment. This could be followed by a counter assault in the form of a defense weapon or a separate and hence exchange of hostilities happen in this phase. The weapon could still remain in stealth mode during this phase and attacks the target. It has a much bigger footprint than when it first entered the target, it has identified the vulnerabilities and knowledgeable about the target. In comparison with the Hostilities phase of CASCON kinetic warfare, the weapon might not reside in the target although it could attack it in stealth mode.The Obfuscation phase is where the mission has been accomplished to the extent to which it was successful and then the Cyber weapon hides or self-destroys.The Withdraw phase is when the parties go into an agreement phase with or without the help of a third party. There is no active weapon on either side.”
A graphical cyber warfare model based on CASCON is displayed below.
As one can observe, it is crucial to understand when these geopolitical ‘new disputes’ or ‘ongoing disputes’ can be observed or detected. It is essential to trigger those global, regional, or country-related events from a threat intelligence perspective. Another important element to note is that cyber warfare missions can be successful without further escalation as they often go by undetected. This is what makes cyber so attractive compared to kinetic warfare, resulting in physical conflict among the states.
According to the framework, a nation-state adversary group will be tasked with missions to other nations with different objectives. This could involve economic espionage, military or political intelligence. The tasking of different missions is perfectly described in the book “Attribution of Advanced Persistent Threats” by Steffens.
Gazula concluded his thesis with the following:
“The CASCON based analysis for cyber-incidents not only revealed insights into what actually happened during a cyber-incident, but helped answer key questions that could potentially cover some predictive behavior of involved states and conflicts in a region.”
This is where cyber threat intelligence exploitation on Twitter might come into play. Twitter users want to share or report information (tensions), seek information, and belong to a certain group [1].
Cyber Threat Intelligence on Twitter
Threat intelligence is a process that consists of several phases, and it starts with a strategic direction. What type of information is the client interested in, and to which questions do we need to provide answers? This is a crucial phase as this starts the intelligence cycle and focuses on the things that are really important and which are not.
The exercise can be a very customized process. It is also leveraging multiple sources, like internal data sources (centralized logging from valuable computer systems, malware detections, etc.), external and internal information on vulnerabilities, exploits, or offerings on the dark web. It also depends on the organization's maturity and what level of detail you are implementing threat intelligence.
An interesting CTI approach can be found on the community-driven VULDB website, which includes an interesting scoring model on the social interest, which is an element that leads to a calculation of the price of the exploit.
To track nation-state actors, mature organizations will also focus on discriminating malware artifacts. Nation-state actors often use malware to lure employees into so-called phishing attacks. The actor drafts an e-mail, usually containing a document with a malicious macro. An example of such a malicious macro routine is displayed in the Armenian case below. After the user clicks and activates the macro, a so-called second stage malware (backdoor) will be installed, which provides the actor access to the system and files.
Some analysts track how these specific encryption mechanisms in the backdoor are implemented via so-called YARA-signatures (Yet Another Recursive Acronym). Threat analysts will focus on these unique encryption routines of the malware as they can be used to track a certain actor group. To maintain intelligence on those actor groups, the threat analysts implement their own specific intelligence cycle. Others will focus on which attack infrastructure these nation-states are actors leveraging and their techniques and typical behavior. So intelligence is usually obtained from different sources.
From a defending perspective, you know that nation-state actors will be tasked to obtain mailbox access like recently was shared in multiple public reports on the SolarWinds breach.
So, what type of information on your e-mail infrastructure do you need to obtain to protect it from being hacked by nation-state actors? It is these questions that drive your intelligence requirements.
These intelligence requirements are then translated into keywords, patterns, custom YARA or snort rules, and relevant data collected from several sources or feeds (internal and external). Analysts will assess the data to determine if there is a course of action (gap) for relevant clients. If that is the case, the intelligence product will be disseminated to the client. The analyst will request feedback if the product was actionable or the requirements needs adjustment. And then the intelligence cycle repeats.
One of the requirements for intelligence is that it is accurate, timely, and provides context on relevant events. Scientists and open source intelligence (osint) practitioners from nine different NATO countries shared that the following could be obtained for social media during a conference in 2012.
Now let’s focus on the intelligence cycle applied to Twitter data. A simplification of the threat intelligence cycle applied to the Twitter data is displayed below.
Building reliable intelligence requirements per topic
So how would you detect such uprisings, drone attacks, diplomatic tensions, weapon investments, or border escalations on Twitter as listed in table 1? Twitter users usually use signal words when describing a phenomenon. In cyber threat intelligence, some of these keywords are “sha256” (usually used for malware samples), “C2” (specifying a command and control servers used by actors), or “exploits.” To make these keywords actionable and reduce the noise, you need to bring them in relation to a certain topic, like malware or vulnerability, for example. It is this journey with your clients to understand what to look for.
As this article focuses on detecting geopolitical and nation-state hacking activity, that’s our current focus. A known Department of Homeland Security (DHS) document gives insight on interesting trigger words used in a homeland security perspective.
What would be relevant “trigger keywords” to detect geopolitical or diplomatic tensions? Based on some professional judgment (I’m the analyst and client in this story), I compiled a list of 50 relevant “trigger keywords” and match them daily on Twitter data. Some of the keywords are listed below.
Keyword matching can be done via several open-source tools like ‘Twint,’ ‘snscrape,’ or via the provided API of Twitter. Recently Twitter shared that its entire Twitter data collection will be available for academic researchers.
Building a relevant list of “trigger keywords” per intelligence topic can be a bit of a cumbersome task. Some keyword matches are shown below and demonstrate the difference in results between using the hashtag(#) sign.
twint -s "#botnet" --since "$yesterday" | wc -l = 31 resultstwint -s "botnet" --since "$yesterday" | wc -l = 1182 resultsYou do not want to collect too much data, but you also do not want to miss too much data. Test the new keywords before applying them into the process and correlate them where possible. Also, keep in mind that these keyword lists are dynamic, English, and based on the intelligence cycle. The list is never complete, and the results are biased.
With some simple automation tasks, the results can be stored in a database or elastic search database per day with the ‘Twint’ tool. A recent overview of my daily threat intelligence collection stats is displayed below. Although the threat actor “trigger keywords” currently contain 108 keywords, it is far more specific than the geopolitical keywords, resulting in fewer results.
Completeness or accuracy of the keywords matches from the ‘Twint’ or ‘snscrape’ tools versus Twitter API results, or manual Twitter search results have not been part of this project. The focus of this article is only on the matches collected.
After the data is matched, the matched tweets are stored in a database or an index search solution like Elastic Search. The value of storing the matched content in a database or index solution can perform historical or additional data analysis. The matched content usually contains information on the country where the event happened or which methods were used. This means that you can also produce reports per country or region and actor.
Verification of intelligence
Before using the content in any form of a threat intelligence product, the events need to be verified. This means verification of the message. First of all, be very skeptical. A good starting point is basically to assume that the message or tweet is fake news. You basically need to prove it is not. Apply falsification theory from Popper to it. Who are the source and author? Is this a legitimate website? Are dates correct? Can the information be found anywhere else? How credible is the statement? Has evidence been supplied? In Cyber Threat Intelligence, usually, so-called Indicators Of Compromise (IOC) are shared. This is seen as artifact evidence of a compromise and can reveal many things about the malware that has been used by the actor or infrastructure they have been using. Just verify or test until you are certain and have multiple sources. Sometimes big media outlets make verification errors or statements as well without actually sharing any evidence. So also be very cautious on those sources as well. In the next article, I will propose using the Anchored Narrative Theory (ANT) to test news articles' intelligence by applying that theory to them.
Once you have found something relevant and matches the intelligence requirements, compile a relevant and actionable report and disseminate it. The final step is to ask for feedback, adjust your requirements and repeat. For now, let’s look back on 2020 and assess what has been found.
Geopolitical Cyber Threats
In this paragraph, three cases will be covered that could provide interesting insights into the correlation between geopolitical tensions and potential nation-state cyber activity. I will briefly demonstrate which “trigger keywords” matched and if other cyber events might be related. Usually, several Twitter users are retweeting the same message. I will only address the geopolitical dispute. Not its background. I will use the ‘Status Quo State’ or ‘Non Status Quo State’ status per nation where possible.
Case 1: Indian-China border dispute
On May 12, 2020, the following geopolitical keywords triggered on Twitter data: “tensions, border” by a user called “ketan72” with the following message.
Tensions remain high in Ladakh, as India braces for 'hot summer' along border with China. #IndiaCheckmatesChina https://economictimes.indiatimes.com/news/defence/tensions-remain-high-in-ladakh-as-india-braces-for-hot-summer-along-border-with-china/articleshow/75692220.cms …ketan72 2020-05-12The article in the tweet was assessed and verified with other sources. Even earlier by the BBC on May 10.
On May 29th, 2020, the BBC published a background report on the border dispute between the nations that also involves building competing for infrastructure in the region. On June 16, 2020, the tensions rose so high that more than 20 Indian troops died in the conflict.
On the 24th of June 2020, the following tweet by “ReflectingMan” was collected on the geopolitical keywords “border, tensions, cyber attack.”
Amid border tensions, spurt in cyber attacks from China as over 40,000 cases recorded in five days, India News News | http://wionews.com https://www.wionews.com/india-news/amid-border-tensions-spurt-in-cyber-attacks-from-china-as-over-40000-cases-recorded-in-five-days-308058 … ReflectingMan 2020-06-24The website in the tweet could be verified in an article from Indian Today on the same date. Basically, the Indian Today shared a similar tweet on the same day with their own news article.
Another story about this cyber attack was shared on the 26th of June by Indian Today. It was alleged that India was being attacked by entities traced back to Pakistan, North Korea, and China. According to sources within the Indian government, known Advanced Persistent Threat actors (APT) “Stone Panda” and “Gothic Panda” groups were active in these attacks. In the article, some references are made to a statement of the Indian Computer Emergency Response Team (CERT). Still, that message seems to be related to a malicious COVID-19 campaign executed by the allegedly North Korean Lazarus group. Some IOCs of that campaign were shared in a referenced site of the Indian CERT.
Although this border dispute is an on-going dispute between India and China, the correlation between the geopolitical border dispute and an uptick in cyber attacks is interesting. It seems that China is the “Non Status Quo State” according to the CASCON framework from a cyber perspective, but there might have been provocations from an Indian side that have not been shared, found, or reported on.
Case 2: Grand Dam dispute between Egypt and Ethiopia
On the 27th of June 2020, the user “DanDomingx”, triggered the geopolitical keywords “cyberwarfare, cyber attack”.
Cyberwarfare in Africa. #africanstudies #twitterstorians https://qz.com/africa/1874343/egypt-cyber-attack-on-ethiopia-is-strike-over-the-grand-dam/ …DanDomingx 2020-06-27The article and the dispute were verified here by the BBC and hereby Yahoo Finance. The story was also confirmed by the Ethiopian Information Network Security Agency on Facebook, naming even more actors, namely ‘AnuBis.Hacker’ and ‘Security_By_Passed.’
The story's background is that Ethiopia is building a Grand Ethiopian Renaissance Dam (GERD), with Chinese support, which would generate electricity and control the sole water source for irrigation for Egypt. Tensions between the countries are growing since the building of the dam. The same tensions can be observed in China building a dam on the Mekong river. Whoever controls the water gains a lot of power.
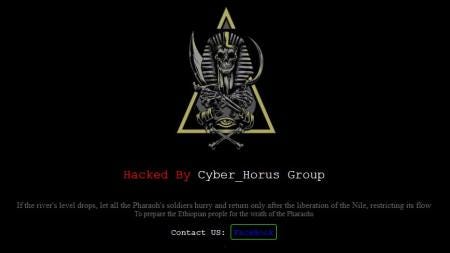
According to the published article, hackers from “Cyber_Horus Group” were responsible for attacking Ethiopia’s political and economic infrastructure. Tensions between the nations started years ago, intending to build the hydroelectric dam.
No link was provided between the hackers and the Egyptian government, but that article states the following:
“Egypt has a history of threatening military action against states that contemplate building dams on the Nile River. In 1979, Egyptian president Anwar Sadat stated that “the only matter that could take Egypt to war again is water.”
From a CASCON perspective, this is also an on-going dispute between Egypt and Ethiopia. Still, the GERD tensions definitely spiked up a cyber element from the “Non Status Quo State” Egypt. It remains unclear if this was driven by the nation, though.
Case 3: Nagorno-Karabakh war
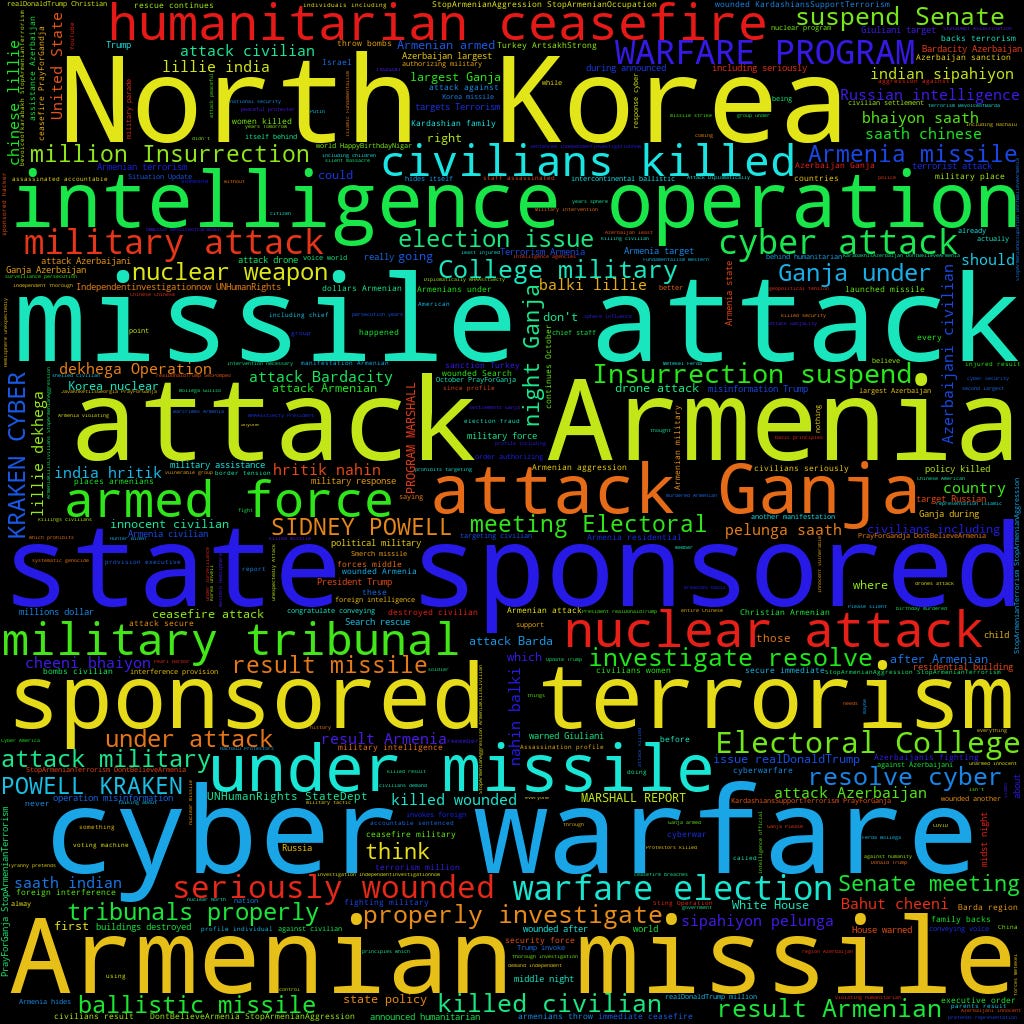
As perfectly illustrated with the word cloud picture on the cover of this article, many “chatter” on Twitter was collected between an on-going dispute between Armenia and Azerbaijan in the final quarter of 2020. Word clouds can be used to quickly assess a lot of information as they highlight the frequency of the displayed word's size.
On 27 September 2020, serious clashes in that disputed region erupted after initial clashes happened in July 2020.
By 8 October 2020, the Twitter user. “shanvav” triggered the geopolitical keywords “espionage operation, cyber-operations”.
"As the Azerbaijan-Armenian fighting continues, hackers are targeting Azerbaijani government and diplomatic entities in an apparent espionage operation, showing how cyber-operations can coincide with physical conflict, @snlyngaas reports @CyberScoopNews https://t.co/lM6qqY99Lt" The article from CyberScoop news alleges hackers were targeting the Azerbaijani government with malware dubbed “PoetRat” as the malware contained references to the famous Russian author Fyodor Dostoevsky as can be read in the screenshot below.
The article mentioned was verified by assessing the source Cisco Talos. They also shared IOC’s and referred to another campaign in April 2020.
An earlier article from journalist Samvel Martirosyan 2018 alleges that Armenia is at the center of state-sponsored attacks. Based on the CASCON framework, it seems that Armenia is a “Non Status Quo State” from a cyber perspective.
Conclusion
Geopolitics is the global competition between nations, and it is sometimes a messy one, which could result in disputes or armed conflicts. Attacking other countries is an ideal way to increase your own economic interests, but it can also bring great disruptive power. The latter can still easily be denied.
From a cyber threat intelligence point of view, it is key to detects these disputes as it might help your threat assessments and detecting these nation-states in your organizations or countries. Are you aware of the geostrategy of other nations?
Of course, this analysis is far from complete as more intelligence needs to be collected to substantiate an alternative perspective. Maybe another nation started the cyber dispute, but no reports have been made public about it yet, or I did not look good enough. As mentioned earlier, the preferred way is to obtain intelligence from multiple sources. The benefit of Twitter is that many users are reporting relevant information fast and belong to a similar group. Sharing is caring!
The collected Twitter data is precious from a CTI perspective as it turns out to be very timely, actionable, and provides context. An analyst can use the collected data in-country or regional assessments. By collecting Twitter data, as demonstrated in the article, also reduces your screen time in the Twitter app as it brings focus:). Several open-source tools can provide you access to Twitter data, but some also sometimes have some stability issues. Obtain access via the Twitter API seems the preferred way, but it also has some limitations for ordinary users.
However, by applying this approach, I have learned many new interesting insights around conflicts or disputes. This article only covered three cases, but there have been many more. Before starting this personal project, I would not have known about the tensions between Ethiopia and Egypt around the GERD dam or that a similar dispute can be observed with a dam controlling the water flow in Vietnam by China.
This effort has broadened my horizon and also brought new areas or actor groups that triggered my interest. I have concluded the intelligence cycle by updating and adding new trigger keywords.
A potential area for improvement from a Cyber Threat Intelligence (CTI) perspective is and is in line with the MICT’ MICTIC framework, including geopolitics as a topic in our cyber threat assessments and assess nation-state attribution holistically. Why is this attack occurring, who is benefiting, and what is the evidence? In the next article, I will use the Anchored Narratives Theory to investigate regular allegations about the involvement in hacking operations. Who is claiming that ”sources close to the government as saying that country X is responsible for a certain attack”? Let’s try to understand with what type of evidence these stories are anchored on.
And finally, remain vigilant for malware when assessing these triggered tweets. It might happen that someone is exploiting your interest, as we have seen recently with alleged North Korean actors targeting cybersecurity researchers on 27 January 2021.
Please let me know if you have any suggestions, corrections, or comments.
References
2012, Estabrooke, I. and D.J.Y. Combs, Social Media Defining the Problem: A Research Perspective, in HFM-201 Specialist Meeting on Social Media: Risks and Opportunities in Military Applications, R. NATO, Editor 2012: Tallinn, Estonia
2013, Bruce Forrester, Twitter as a Source for Actionable Intelligence
2014, Bruce Forrester, Providing Focus via a Social Media Exploitation Strategy
2016, Marie-Eve Jobidon & Bruce Forrester Understanding Social Media Networks through Trending Analysis
2017, Mohan B. Gazula, Cyber Warfare Conflict Analysis, and Case Studies
2012 ET.BY, Technical Activity Proposal -Intelligence Exploitation of Social Media, 2012, NATO RTO.