The Trojan did it defence is real!
A historical deep dive in planting digital evidence by nation-state actors to incriminate political opponents.

Disclaimer: The views, methods, and opinions expressed at Anchored Narratives are the author’s and do not necessarily reflect my employer’s official policy or position.
Introduction
Last week, cybersecurity company SentinelOne released an interesting report detailing a decade of a mass surveillance program by alleged nation-state hackers from India, dubbed ModifiedElephant. The majority of their intelligence findings originate from the digital forensic work conducted by a US forensic firm called Arsenal Consulting, hired by the defendants in a case called the Bhima Koregaon case.
Arsenal Consulting analyzed the electronic evidence seized from Rona Wilson and Surendra Gadling. However, the court refused to issue a search warrant to search their residences. Still, on April 17, 2018, the Pune police raided the homes of activists Rona Wilson and Sudhir Dhawle and seized their computer’s hard drives and USB drives.
In the computer of Mr. Wilson, the police found multiple files of meetings with Maoist militants and documents detailing a conspiracy to assassinate the Prime Minister of India, Narendra Modi.
Arsenal Consulting investigated those seized computers that the Puni Police took. As it turns out, Mr. Wilson’s computer was compromised 22 months earlier. A Netwire backdoor was installed by a threat actor. The alleged nation-state actor planted 24 incriminating documents in a hidden folder on Mr. Wilson’s computer.
The president of Arsenal Consulting, Mr. M. Spencer, states in their report 1: “It should be noted that this is one of the most serious cases involving evidence tampering that Arsenal has encountered, based on various metrics which included the vast timespan between the delivery of the first and last incriminating documents.”
According to the Arsenal Consulting report I dating of 2021-02-08, Mr. Wilson has been imprisoned since his arrest on June 6, 2018.
Besides my full-time job at Volexity, I’m also an assessor for the Dutch Expert Witness register in digital forensics, so this case interests me greatly. In this case, we have a clear case of the “Trojan did it defense” which appears to be true, and what might happen to you if you are seen as an activist or political opponent by your government.
In this Anchored Narrative, I will explain what the so-called Trojan Horse Defence is, discuss earlier cases, and some crucial pieces of evidence in the analysis of the reports by Arsenal Consulting. This anchored narrative will also address some concerns for the future and some (forensic) recommendations that you can take. I expect that this “Bhima Koregaon case” has already been sold as a Hollywood movie script as the reality of the entire case feels so surreal. Having spent some time on the reports of this case during this weekend, I’m also a bit frustrated why I have missed the reporting on this case entirely, but let’s go.
What is the Trojan Horse Defense in cybercrime cases?
The “Trojan Horse Defense” is a technology version of the Some Other Dude Did It (SODDI) claim. The defendant typically denies any responsibility for the presence of any incriminating material (contraband) on the defendant’s computer because malware or any other program that provides access to their computers is responsible for the creation of that material by another perpetrator. This defense strategy often happens in cases of hacking or the presence of child pornography. The term originates from a case in the United Kingdom in 2003.
The first successful use of the Trojan Horse defense was in the case Regina v Aaron Caffrey from 2003 in the UK, where Caffrey successfully was acquitted from a denial of service attack against to port of Houston.
But the Trojan Horse Defense was usually seen by the prosecution as a defensive strategy by a suspect responsible for the committed acts. Also, the plan has not always been successful in courts.
Some other interesting planting evidence cases
In this section, I will highlight a short summary of some other cases where potential nation-state surveillance was in play, were evidence was fabricated, planted or both.
2010 Stalker jailed for planting child porn on a computer
In 2010 a suspect broke into the house of a co-worker. The suspect wanted to have a relationship with his co-worker's wife, so he used their family computer and downloaded child pornography on it. After which, the suspect removed the hard drive and mailed it to the police. Although the co-worker was initially arrested, the suspect also made a copy of the hard drive's contents before sending it to the police.
Although no trojans were used, this was a case where someone else committed the crime.
2012 Sharyl Attkisson’s computer intrusions
In 2012, Sharyl Attkisson, a highly respected investigative journalist working for CBS at that time, was allegedly targeted by the US government for her scoops on the ATF and a Benghazi elite security team that left the Embassy a month before the raids.
According to a Washingtonpost article, Don Allison, a security specialist at Kore Logic who examined the iMac of Mrs. Attkisson a great deal of her system was expertly wiped, but was able to find remnants of a sort of backdoor government computer connection to her computer.
According to her reporting, both her CBS Toshiba laptop and her iMac computer were forensically examined, and multiple traces were found of these intrusions.
The breaches on Attkisson’s computer, says this source, are coming from a “sophisticated entity that used commercial, nonattributable spyware that’s proprietary to a government agency: either the CIA, FBI, the Defense Intelligence Agency, or the National Security Agency (NSA).” Attkisson learns from “Number One” that one intrusion was launched from the WiFi at a Ritz Carlton Hotel and the “intruders discovered my Skype account handle, stole the password, activated the audio, and made heavy use of it, presumably as a listening tool.”
To round out the revelations of “Number One,” he informs Attkisson that he’d found three classified documents deep inside her operating system, such that she’d never know they were even there. “Why? To frame me?” Attkisson asks in the book.
As with the Bhima Koregaon case Attkisson claims in her book called Stonewalled, that three classified documents were found on her operating system without her knowledge.
The difficulty in assessing Attkisson’s claim that no actual digital forensic reports are published to understand the digital forensic details, which is the total opposite of the Bhima Koregaon case, which we shall discuss a bit later.
2021 The Pegasus Project and cyber-surveillance by the NSO group
In July 2021, the news broke from a ‘data leak’ with 50.000 mobile phone numbers of potential surveillance targets. More than 180 journalists worldwide were targeted by the Israeli company NSO Group which sold its mobile surveillance technology, called Pegasus, almost exclusively to nation-states. The infamous NSO Group is also responsible for creating the most advanced backdoor called ForcedEntry for IOS devices. According to Amnesty, these targets of the NSO group include heads of state, activists, and journalists, including Jamal Khashoggi’s family. Amnesty released a report on how they forensically examined the attacks on several targets.
In the earlier discussed Bhima Koregaon case, Mr. Wilson’s iPhone, the defendant was also targeted with NSO Groups Pegasus in 2017. The usage of Pegasus indicates nation-state involvement. India was likely a customer of the NSO group.
2021 Odatv case EGOMANIAC in Turkey
Again Arsenal Consulting's forensic expertise was requested in a court case in Turkey where journalists were initially arrested, and attackers were the source of pushing incriminating documents on those systems used to justify arrests by the Turkish National Police. Based on the forensic work of Arsenal Consulting, a court acquitted the journalists in 2017.
According to the report on EGOMANIAC by SentinelOne, the threat actor behind the attacks on the journalists operated during the 2010-2016 timeframe, where they primarily focused on Turkey and Turkish politics. Victims were lured via e-mail with zip files containing an executable, after which a backdoor was installed.
Although a full forensic report has not been released by Arsenal Consulting in this case, the report on EGOMANIAC contains a tremendous amount of details of an alleged nation-state actor who is well funded (customer of the infamous Hacking Teams Remote Control System) and persistent but also relentless in incriminating political targets by placing fabricating document.
2022 Bhima Koregaon case in India
Before we continue, if you are a digital forensic analyst, researcher, practitioner, or lecturer, you must read all four Arsenal Consulting reports (1,2,3,4). The forensic reports that have been produced provide insights into how evidence was found on the investigated material and how the evidence could be reproduced with the same evidence by any other investigator.
This subsection will highlight interesting evidence from one of the four reports that prevent Mr. Wilson from producing the forged documents.
Mr. Wilson got compromised on June 13, 2016, by a phishing e-mail from someone who had access to Varavara Rao’s mailbox that appears to be a Dropbox link but was a rar archive containing the NetWire remote access trojan.
Arsenal Consulting recovered five NetWire samples from Mr. Wilson’s computer, two of which were still active on the file system.
The actors who targeted Mr. Wilson also used other tools to sync local files from the computer with the command and control server, as shown in screenshot 4.
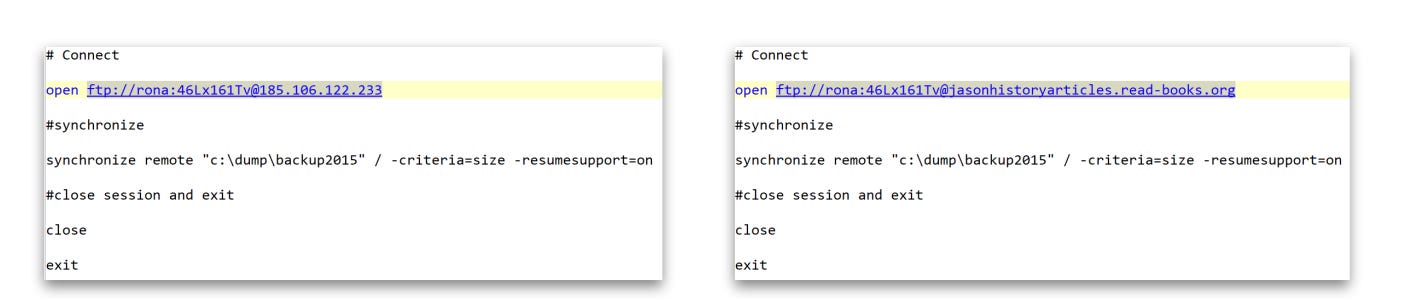
Although several tools were used to clean the system, antivirus software also detected some versions of NetWire. Additionally, Arsenal was able to recover NetWire logs from the computer of Mr. Wilson. These recovered logs provide insights into Mr. Wilson visiting certain websites, submitting passwords, and editing documents like in screenshot 5.
But the most exciting piece of evidence in favor of Mr. Wilson is that the incriminating documents allegedly authored by him that the nation-state actors placed were generated with Microsoft Word 2010, and Mr. Wilson only used Microsoft 2007. The actor saved the incriminating files were saved to PDFs by the actor with the version used of Microsoft Word 2010 or Word 2013. An excerpt of fabricated files that the actor has placed on the computer of Mr. Wilson can be seen in screenshot 6.
The Trojan Solved it!
In 2009, while working at Hoffmann Investigations, I wrote a piece for SANS called The Trojan Solved It. The case details a forensic investigation of an employee selling assets from the company on the Internet for personal gain. He got warned and deleted a considerable amount of evidence, except evidence captured by a piece of malware that recorded his fraudulent actions perfectly in an Alternate Data Stream. Alternate data streams are a functionality within NTFS that allows files to be associated with more than one data stream.
Like the cases mentioned above, proper digital forensic analysis needs to be conducted that investigates multiple investigative scenarios, one of which has to be “The Trojan did it, or someone else did it.”
Recommendations
If you belong to these targeted professions, make sure you follow proper Surveillance Self-Defense guidance instructions from the Electronic Frontier Foundation.
Besides following proper self-defense guidance, the time has also come to make sure that digital forensic practitioners capture the memory of the computer systems always and first. It is the best practice and should be mandatory in every digital forensic investigation.
Even if it has been rebooted, it helps the forensic investigator understand if the computer was running in a trusted state. Yes, after a reboot, a lot of valuable evidence is lost. However, there might be persistence mechanisms of malware or any other backdoors still running on the computer system of interest, which can also and easily be found via the analysis of memory.
Although the level of sophistication of these nation-state actors seems low, it is likely that other nation-state actors work more advanced and potentially leave fewer traces on the file system, making a case for memory forensics even stronger.
The amount of traces, malware, relevant artifacts, or manipulated system service descriptor tables that can be obtained from memory with tools like Surge or Volcano is something I experience daily.
Make it your default practice. Perform MemoryForensics, always!
Conclusion and concerns
In this anchored narrative, several cases were discussed where alleged nation-state actors surveilled their victims for months or even years and then planted evidence on their computers. In the case of Mr. Wilson, the proper digital forensic examination was conducted by Arsenal Consulting, but how many victims globally did not receive the same amount of support and have been jailed by falling victim to these nation-state actors? That said, Mr. Wilson spends a lot of time behind bars already. I’m not even sure if he has been released?
Also, the sophistication of the discussed cases by the nation-state actor was not advanced but against illiterate computer users more than enough. It seems likely that advanced nation-states also employ the same tactics against political opponents. That said, Mr. Wilsons’ iPhone was also targeted by the infamous spyware Pegasus produced by the NSO Group, a highly advanced piece of malware.
Both the ModifiedElephant and the EGOMANIAC actors are directed by their leaders to spy and eventually plant evidence on their political opponents, but who ordered these surveillance operations and created the fabricated documents? And the most worrisome finding of these reported cases is that innocent people are being put behind bars, some for several years.
Until the next anchored narrative.








