Recover your files with StrongPity
A case study of a multi-year nation-state cyber surveillance campaign
Disclaimer: The views, methods, and opinions expressed at Anchored Narratives are those of the author and do not necessarily reflect the official policy or position of my employer.
Introduction
First, a warm welcome to the new subscribers of the Anchored Narratives mailing list. For the ones who are new to the list, I regularly pick an exciting tweet that matched my intelligence requirements and generated anchored stories on geopolitical (cyber) threats, digital forensics, and crime from that. Usually, I pick a story that I have no real in-depth or prior knowledge about. The goal is to understand a particular topic better, improve my investigation or writing skills, and generate a reliable story anchored with evidence. This time the story will start with a tweet that matched my intelligence requirements on 15 March 2021:
"#apt #strongpity new sample hunted md5:95ff679f525c44e4abac8e61f8052ca5 c2:transferprotocolpolicy.com"The information in the tweet tells people with interest in this field that someone found a malicious malware sample with a unique value “95ff679f525c44e4abac8e61f8052ca5” from an Advanced Persistent Threat actor group called StrongPity. APT is an industry name for referring to states involved in cyber operations. The referred malware sample communicates to its command and control server “transferprotocolpolicy.com” (c2) for further instructions. This tweet triggered some personal interest to start a deep dive into this nation-state actor group. They have been around for many years, deploy interesting tactics at scale, and are observed in geopolitical disputes. This article will outline the background of this alleged Turkish nation-state actor or nation-state-sponsored group. Furthermore, the malicious backdoor will be reversed briefly and based on that intelligence to hunt for additional indicators, and finally, the article will end with some observations and a conclusion. Let’s go.
Background StrongPity
The StrongPity actor group has been around since 2012 and employs the same tactics, namely adding backdoors to legitimate software used by specific users. Some call this technique water holing. The group is also referred to as APT-C-41 and PROMETHIUM. In 2016 StrongPity was detected by Kaspersky in a campaign that targeted specific users in Belgium and Italy who were interested in Truecrypt and Winrar software. The software packages are used by niche user groups interested in solid encryption. The actor group set up a domain name that mimicked the official WinRAR distribution site and placed links to the trojanized WinRAR installer on a certified distributor website. In the same year, Microsoft observed a campaign by the same group targeting specific users with a zero-day vulnerability in Adobe Flash. The zero-day exploit was tracked as CVE-2016-4117. In 2017 ESET published research where they detected StrongPity while tracking the FinFisher group and an Internet Service Provider's involvement. Their analysis revealed that users were redirected to trojanized software packages. Some of the targeted software were the following software packages.
CCleaner v 5.34Driver BoosterThe Opera BrowserSkypeThe VLC Media Player v2.2.6 (32bit)WinRAR 5.50
In their research, ESET states that an exfiltration component in the StrongPity backdoor collects files with the following extensions:
.ppt,.pptx,.xls,.xlsx,.txt,.doc,.docx,.pdf,.rtf
The stolen files are sent to a central server operated by the StrongPity actor, and the backdoor waits for further instructions.
By 2018 Citizenlab found several so-called deep packet inspection devices in Türk Telekom's network where users were redirected to download trojanized installers Avast Antivirus, CCleaner, Opera, and 7-Zip. The surveillance was set up so that users who searched for official downloads on the authorized vendor websites were silently redirected to the trojanized versions of Avast, CCleaner etcetera. Citizenlab referred to the malware as StrongPity, which was used after they stopped using FinFisher spyware. FinFisher was sold to governments as a lawful interception capability. Citizenlab also described that these injection techniques were also observed by other nation-states, China (Great Cannon) and the US (NSA’s QUANTUM).
In June 2020, Bitdefender published research where StrongPity employed similar tactics to infect victims in Turkey and Syria selectively. According to Bitdefender, the group was specifically interested in the Kurdish community giving it a geopolitical angle.

In their investigation, Bitdefender found trojanized versions of the following software:
7-ZIPWinRARMcAfee Security Scan PlusFile recovery application - RecuvaTeamViewerWhatsAppCCleanerCleverFiles Disk DrillDAEMON Tools Lite
They also found a particular tag used as authentication and is influenced by the file's compilation time. These tags could look like something like “v11_kt26“ for example. To me, these tags resemble campaign identifiers used by actors to distinguish between different targets. The researchers from Bitdefender added a tremendous amount of StrongPity samples in their report indicating an extensive campaign.
Researchers from Cyble released a report in December 2020 that the StrongPity actors expanded their global reach and included mass phishing e-mail campaigns. According to their research, victims were now widespread across Europe, Nothern Africa, Canada, and Asia. Cyble discovered that the victim was targeted through a trojanized version of the Partition Find and Mount software utility. Their analysis refers to a screenshot (figure 6) that should demonstrate the decryption routines and decrypted payloads in the process memory. Especially those screenshots are blurred and not readable. After that, they report that the malware creates a mutex1 with a particular name (figure 7) and then how the malware connects to a specific domain in a debugger (figure 8). It remains unclear how the mutex's name is generated and where and how the command and control information is stored from their research. The claim of mass phishing attacks is not substantiated by e-mail samples in their report. Their released StrongPity indicators already contain the “transferprotocolpolicy[.]com” as a command and control server that matched the starting tweet, which matched my intelligence requirements in March 2021.
In 2021 LMNTRIX released research into what they call “the Turkish APT group APT-C-41 (aka StrongPity and Promethium)”. They claim that the group targets Financial organizations, Industrial plants, and Educational institutes after installing a backdoor on its victims. Their research provides some screenshots of a disassembly tool in which they state that the malware has so-called anti-debugging functionality enabled (IsDebuggerPresent check).
They further state: “After bypassing these functions, we found the command and control domain embedded into the code. The snapshot shows the communication happens to the malicious domain, which we highlighted below [mailtransfersagents(dot)com]:”
The malware samples referenced in their research are indeed StrongPity samples. Based on the screenshots LMNTRIX provided, I could not observe the command and control domain embedded in the provided snapshots.
Both reports of Cyble and LMNTRIX triggered me to dive into some reversing of the backdoor functionality to determine how the StrongPity backdoor stores its configuration, as this was not clear to me from their analysis. Let’s start with the sample that triggered my intelligence requirements in the first place.
Reversing the StrongPity backdoor
The StrongPity backdoor is installed via trojanized installations of legitimate and popular software products. The extensive research of Citizenlab indicates that a Telecom provider in Turkey was involved in the redirection to the trojanized downloads to its victims.
What is not clear to me is how the configuration data is stored in the malware. To understand how that data is stored, I will follow the regular malware reversing process. You start with static analysis. What information can you get out of the malware sample without executing it? If things are not evident by then, you can also execute the malware in a sandbox or run it in a so-called debugger. For readability, I will only focus on the main findings.
Static analysis
Usually, you’ll start looking at which ‘strings’ (text) are present in the malware sample. Analyzing strings in binary files is an essential aspect of malware analysis. This technique provides valuable information about the program’s use and its functionality. Usually, string output is used to develop Yara signatures. Yara is a tool to identify and classify malware families. Unique strings, constants, or byte patterns are used in the so-called Yara signatures to find more samples. Usually, these signatures hold indicators of compromise, like filenames or specific user agents observed in the malware samples. Malware authors generally leverage obfuscation or encryption techniques to hide their secrets that they need to store in the binary. They will also employ anti-debugging tricks to hinder automated analysis. To leverage the Windows operating system's functionalities, malware authors often rely on standard Windows Application Programming Interfaces (API) for their backdoors to interact with the system. Usually, these APIs are seen in the ‘strings’ output, but malware authors can also hide this. In the StrongPity sample, many of these APIs were observed, like CreateMutexW, CreateProcessW, WinHttpConnect, and IsDebuggerPresent. The regular ‘strings‘ command on Linux revealed no domain information, however.
To determine if the StrongPity malware authors employed an obfuscation technique called stack strings, the ‘floss’ program was used. That revealed the following information:
The extracted information reveals file names (winmsism.exe. sppser.exe), but also “ndaData“ the directory where the malware collects its information before sending it to the operators, according to the reports. Other than those indicators, I have highlighted some suspicious string patterns. By briefly assessing this output, it looks like this is the config information stored in the StrongPity backdoor. But we need to a bit more digging, and I will use a free open source disassembly tool called Cutter for that. A decompiler is a program that analyzes executable programs and tries to create a high-level representation of the machine code from it. Cutter has a feature to decompile an executable program to reconstruct the source code. This feature helps to understand the analyst's flow and how the malware program calls certain functions or routines. By decompiling the main function of the StrongPity malware, it becomes immediately apparent how the file names and the mutex observed in the floss stack strings output are being passed to the relevant functions.
So the mutex created from the stack strings in the StrongPity backdoor can be seen in screenshot 2.
The file names are also created from the stack-based strings values.
In screenshot 3 the function with the name fcn.0040106a(); is executed. That function leads to two so-called byte encoding algorithms by leveraging a single-byte XOR operation with 0x59 and 0x2b. Malware authors often use XOR as this algorithm obfuscates data easily. XOR is a bitwise operation. If you XOR something twice with the same key, this will result in the original value. In the example below, the capital character “A” will be XOR’ed with the XOR Key “B”. The output data of the XOR operation is a non-printable character (NP). If we then XOR that value with the original XOR key “B” we have the original value back.
Input data = 'A' = 01000001
XOR Key = 'B' = 01000010
Output data (NP) = 00000011
XOR Key = 'B' = 01000010
Output data = 'A' = 01000001As shown in the example above, these operations can result in unreadable information as non-printable characters are not printed or detected by the ‘strings’ or ‘floss’ utilities. Let’s continue with the analysis.
The XOR operation with the 0x59 byte values will eventually decode the encoded stack strings to the first domain and URL, namely “hxxps://transferprotocolpolicy.com/parse_ini_file.php" The XOR operation with the 0x2b byte values finally results in the following domain and URL after decoding “hxxps://transferprotocolpolicy.com/phpinfo.php"
Dynamic analysis
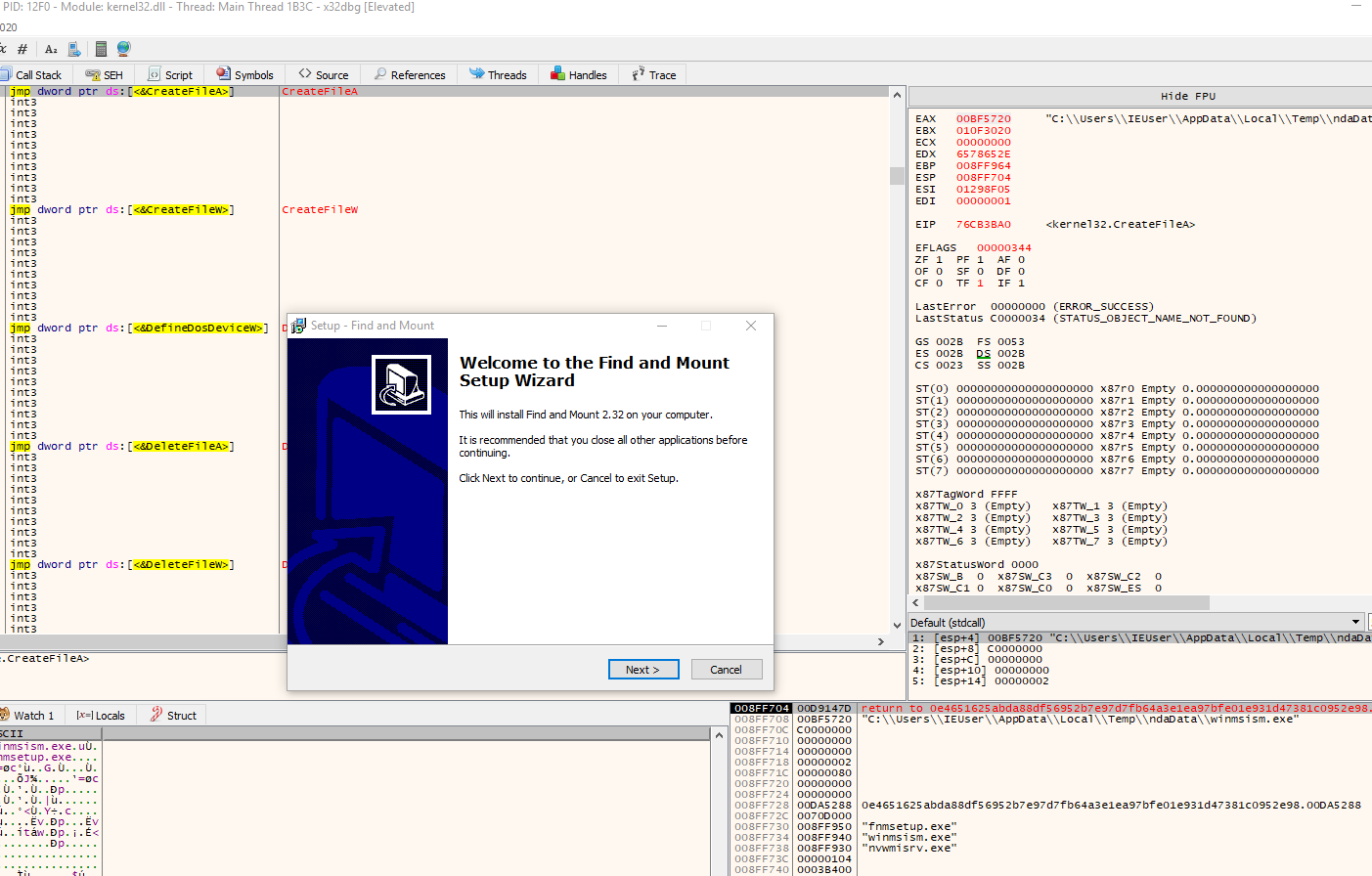
So after the static analysis, the StrongPity sample was executed in x64dbg on my isolated virtual machine for some dynamic confirmation of the initial findings. By setting a breakpoint on the CreateMutexW and GetTempPathW API functions, the StrongPity backdoor reveals the creation of the same mutex and later on deobfuscation of the domains and URL used by the StrongPity actors. I will briefly describe the findings with some screenshots below.
Screenshot 6 displays the stack strings (partially) found by floss, encoding the domain name.
After installing the StrongPity backdoor on my virtual machine, the backdoor immediately starts gathering files based on a certain extension and temporarily stores it in a compressed file “config.bin” before it wants to send it to the command and control server. Some content is displayed in screenshot 8. Bonus question for reversers. Who recognizes the pdf file?
Malware analysis recap
After assessing the StrongPity backdoor with floss, it immediately became clear that many backdoor configuration items are stored in stack strings in the binary, like mutex, directory, file names, and domain information. Potentially to evade normal detection. By leveraging the power of the decompilation feature of the Cutter reverse engineer platform, the single-byte xor obfuscation algorithms were quickly detected.
StrongPity backdoors are good candidates for Yara rules as the backdoors contain many strings, constants, and byte patterns that can be leveraged in Yara rules. Over time the actor behind the StrongPity backdoor makes small updates to the backdoor.
Hunting for more StrongPity samples
Based upon the intelligence gathered by other security companies and by leveraging the power of VirusTotal Intelligence (VTI), you can really start hunting on this adversary. VTI has a great feature called the search for similar samples like these. With that search, the samples below were found. One additional remark, this great publication platform does not support tables, hence the screenshots. If you’re interested in the malware samples, feel free to reach out.
Based on additional Twitter intelligence and using the same functionality, some newer samples were discovered.
As was discussed in the background of the StrongPity paragraph the alleged Turkish nation-state actor leverages popular software. The sample with the value “dfd0f4b821438d8a9277728e42ab58bdc2667aa7173892ffd6ede75a5d5645f5” was installed via a trojanized version of Partition and Mount which was uploaded in Korea. That trojanized version can be downloaded from VT as well with the following sha256 checksum: “0e4651625abda88df56952b7e97d7fb64a3e1ea97bfe01e931d47381c0952e98”
Conclusion
Based on industry intelligence reports and my own brief malware analysis, it becomes clear that the alleged Turkish nation-state actor StrongPity is likely running a massive and multi-year data collection program and is apparently successful. Citizenlabs and Bitdefender reported strong indications of Turkish nation-state involvement. The backdoor received small updates periodically, and the collection infrastructure has been improved over time. The actor was initially focusing on the Middle Eastern region. The actor is now also focusing on Europe, Asia, and Canada. The claims of massive phishing campaigns by Cyble were not substantiated by evidence in their report. The same holds for LMNTR, who claimed that StrongPity targeted Financial organizations, Industrial plants, and Educational organizations after compromising victims' computers. It could be that LMNTR found detections originating from those organizations after some employees downloaded this trojanized software. Still, their research does not explain how compromised victims attacked the referred companies. It would be very interesting if the StrongPity actors are utilizing compromised victim machines in their attacks. Also, the malware research of both Cyble and LMNTR was not very detailed or sometimes blurred out to agree with that research.
Overall, the StrongPity backdoor is well detected by the anti-virus industry. This assumes that the actor is less successful in company networks and is more focused on citizens. This triggered a thought. Do the victims of the StrongPity actor have a working anti-virus solution? I sometimes support friends and family with computer issues but rarely detect a working anti-virus solution on their private computer. Based upon the minimal updates in the modus operandi and sophistication of this actor, I suspect not. The method that the actor employs is a nice one. Who is not downloading these targeted tools sometimes? Under the above conditions, why would a victim know they are downloading a trojanized version of a certain utility. What worries me a bit is the massive amount of data collection and processing infrastructure that the actor needs to maintain. Based on samples uploaded in VT, I assume that large amounts of data are uploaded into their operated infrastructure. The data collected needs to be processed as well to make it actionable. I wonder what kind of data lake the StrongPity actors have. For next time watch out when you want to recover some files and install StrongPity on your system.
1A mutex is usally genererated by malware creators to avoid infection of a system by different instances of the same malware. On Windows a mutex can be created by the Window Application Programmer Interface (API) function CreateMutexW